Business risks from file leaks during workflow
-

File dispersion
Large volume of enterprise files scattered on employee computers, lacking controls
-

Device loss
Device loss during business trips leads to enterprise file leaks
-

Employee resignation
Departing employees take enterprise files, lack of control causes leaks
-

External sharing
Files sent to external vendors; collaboration leads to uncontrolled leaks
Software-defined file protection boundary: non-persistent & offline control
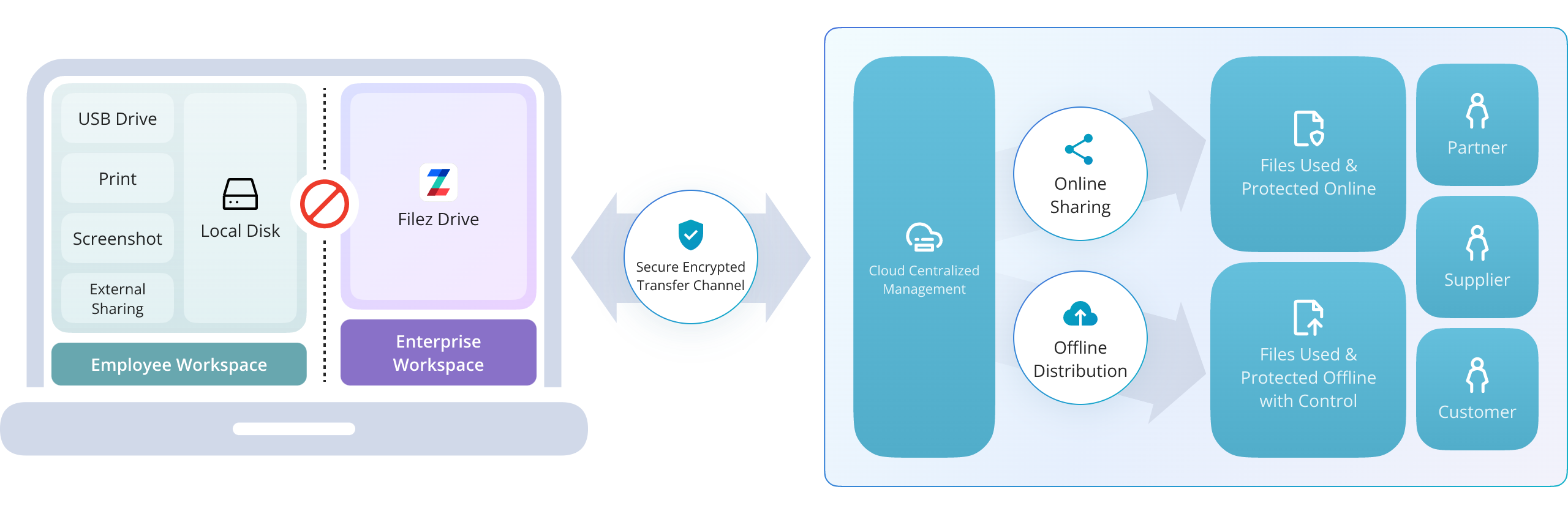
Efficient file application and collaboration
Local operation, online experience
- Fully automatic and directed exchange, achieving 1:1 or 1:many.
- High-concurrency, unthrottled cross-network capability: 5GB in 1 minute.
Full-text file search
- 100% identical local disk file operation experience, no learning curve
- Documents, images, and other formats used directly online, file content not saved locally

Offline control protects collaboration & exchange security

Offline security strategy
- Set offline access duration, bind users and devices, with automatic expiration
- Fully record offline usage processes, enabling audit and inspection of offline behaviors
Offline leak prevention
- Unique offline encryption prevents unauthorized recipient forwarding
- Unique dynamic watermarking prevents screenshot propagation from local files
- Offline files automatically invalidate and wipe from devices upon expiration
Typical enterprise application scenarios
-

Design documents
and code management
-

Customer data
collection & protection
-

Outsourced & temp
staff file access
-

Multi-regional and
cross-team collaboration
Suitable for finance, chip semiconductor, biomedicine, new energy manufacturing and other industries.
Core business value
Online
Fully online content collaboration with secure "non-persistent" files prevents local copies and effectively stops leaks
Online inter-team collaboration prevents screenshot and copy, is auditable, and safeguards sensitive enterprise content
Offline
Secure isolation of personal and enterprise spaces eliminates exchange risks, offering a native drive experience with no extra employee learning
Encrypted, self-destructing files ensure controlled inter-organizational exchange, preventing uncontrolled external offline files
Internal collaboration
External collaboration